If you have purchased Protection PLUS 5 SDK and signed up for a hosted SOLO Server account or purchased SOLO Server, you will need to update your application so it no longer uses our generic SOLO Server Shared URL test account data and instead uses your own Product ID, Encryption Key Data, and potentially your own web service endpoints.
The first step is to log into your account and create a product and a product option.
When configuring your product options, Protection PLUS 5 SDK requires the "Issue Installation ID" option to be checked!
Take note of your Product ID, which can be viewed by using the menu Configure / Products . You will add this Product ID to your source code so it can be validated during activation.
Next, you will need to update your application to use your account's encryption key data. This ensures that only licenses created by your SOLO Server account will be able to activate your software. See our Cryptography and Security topic for more information on how this works.
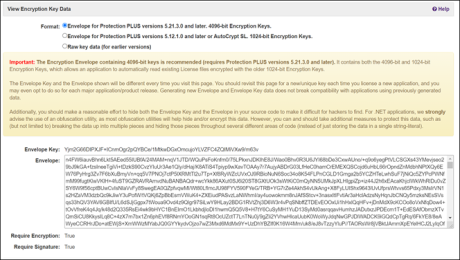
To get this data, go to the menu Configure / Products then use the Actions dropdown to choose View Encryption Key Data. The Format needs to be set to Envelope, and the data in the Envelope Key and Envelope fields needs to be set in your source code.
Be sure to select the correct Envelope format for your application. Applications using Protection PLUS 5 SDK prior to version 5.21.4.0 will need to use the 1024-bit Encryption Envelope data. Otherwise, it is recommended to use 4096-bit Encryption Envelope data.
For your convenience, the Protection PLUS 5 SDK sample applications are configured to use a generic test SOLO Server account encryption key data for your evaluation purposes. This data is not intended for product distribution, and any license created with this test account is automatically deleted. Furthermore, using the generic test account's encryption data in your application would mean anyone could use that same data to manage/bypass your application's license.
In the PLUSManaged sample applications, you will find the encryption key data in the LicenseConfiguration class under the Encryption Settings region.
For information on how to set the encryption key data (and the Product ID), view the topic on Creating the License Implementation for PLUSManaged, or the topic for Configuring the API Context for PLUSNative.
If you are using SOLO Server Shared URL, you do not need to make any changes here since it is already using https://secure.softwarekey.com/solo/ in the samples. In all other cases, following the instructions below depending on which SOLO Server package you are using. In the PLUSManaged sample projects, you would make these changes in the WebServiceHelper class. For additional information on calling the web services, view these topics:
Update https://secure.softwarekey.com to https://[your brand].softwarekey.com where [your brand] is your sub-domain.
Update https://secure.softwarekey.com/solo/ with https://[domain]/[SOLO root]/, where [domain] is your fully-qualified domain name and [SOLO root] is the root directory for SOLO Server.
replace https://secure.softwarekey.com/solo/ with https://[domain]/[SOLO root]/, where [domain] is your fully-qualified domain name and [SOLO root] is the root directory for SOLO Server.
Test all of the web service endpoints in your application thoroughly to ensure everything is functioning properly with the correct endpoint URLs, the correct Product ID, and correct encryption key data.