System identification is where your application obtains some information about the system on which it is running. Typically, any license which requires activation uses information about the system so that the specific system may be authorized. The Protection PLUS 5 SDK APIs assist you with authorizing and validating this information by making several "System Identifier Algorithms" and supporting functions/methods available to you. These algorithms can be used to generate "System Identifiers" using any combination of information including (but not limited to) the different identifiers listed in these topics:
Furthermore, the Protection PLUS 5 SDK APIs are so flexible and robust, they allow you to specify your own types of identifiers.
It is imperative to keep in mind that you are responsible for testing any custom system identifier algorithms you create to ensure that the reliability and uniqueness of the identifiers meet your expectations and requirements.
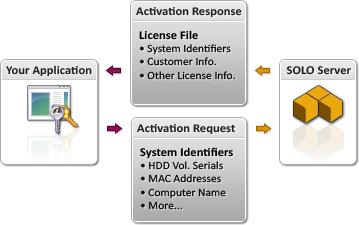
A system is authorized for a license during activation with SOLO Server. This allows SOLO Server to include the information about the system in the license file issued as illustrated below.

To further explain the illustration, here is the full process it depicts:
It is not uncommon for a customer to change some of his or her computer's hardware after activating your software. Changes can occur when components and drivers fail, and it is often (if not generally) ideal for your application to allow for some amount of change without requiring re-activation. The Protection PLUS 5 SDK APIs give you access to the data necessary to compare and contrast information about the system currently running versus the system which was authorized at the time of activation. So for example, if you used MAC addresses from the system's Network Interface Cards (NICs), you might expect the number of NICs present to change on mobile computers or laptops. This is because many laptops might have removable hardware connected and disconnected regularly, which sometimes includes docking stations. With this in mind, your application can leverage the Protection PLUS 5 SDK APIs to ensure at least a certain number of NICs match, as it best suits your application's licensing requirements. Of course, this principle can be applied with any type and combination of system identifiers.
See the Docs article "How can I allow small identifier or hardware changes?" for more information.
Using a large amount of information about a system to authorize it has the benefit of allowing for more flexible matching fuzzy-logic (to allow some acceptable amount of change to occur without requiring a new activation) and allows you to better prevent other, very similar systems from being inadvertently authorized to use the same license file. However, collecting this kind of information could cause privacy concerns for your users. The system identification logic in Protection PLUS 5 SDK and SOLO Server relies on using hashes of information (more about hashes). Using the one-way cryptographic hashes prevents anyone and everyone from using data showing what hardware your customers use for anything other than the intended purpose (system authorization). The Protection PLUS 5 SDK APIs are not designed to enable you to use this data for purposes other than system identification and authorization for licensing purposes, and SOLO Server is also not designed to make this data useful or available outside of the intended capacity.